Have you ever wondered what risk assessment in cyber security really means? In this digital age, where technology is intertwined with every aspect of our lives, it’s essential to understand the concept of risk assessment and its significance in protecting our online world. So, let’s dive into the world of cyber security and uncover the secrets behind risk assessment!
When it comes to cyber security, risk assessment plays a crucial role in identifying and mitigating potential threats and vulnerabilities. It’s like a detective’s toolkit, helping us uncover the hidden risks that could compromise the security of our digital assets. Just like a skilled detective assesses the risk of a crime scene, cyber security professionals assess the risks lurking in the virtual realm.
So, what exactly is risk assessment in cyber security? Well, it’s a systematic process of identifying, analyzing, and evaluating potential risks to our digital systems, networks, and data. It involves understanding the vulnerabilities that cyber criminals could exploit, assessing the likelihood of an attack, and determining the potential impact it could have. By conducting a thorough risk assessment, organizations can develop effective strategies to safeguard their digital assets and proactively respond to any cyber threats.
In a nutshell, risk assessment in cyber security is like putting on a detective’s hat and investigating the vulnerabilities in our digital world. By understanding the risks and taking proactive measures to mitigate them, we can ensure a safer and more secure online environment for ourselves and future generations. So, let’s embrace the power of risk assessment and protect our digital domains from cyber criminals!
Understanding Risk Assessment in Cyber Security
Risk assessment is a crucial process in the field of cyber security. It involves identifying, analyzing, and evaluating potential risks and vulnerabilities within an organization’s digital infrastructure. By conducting a comprehensive risk assessment, businesses can effectively mitigate cyber threats and protect sensitive data from unauthorized access or exploitation. In this article, we will delve deeper into the concept of risk assessment in cyber security, exploring its importance, methodologies, and best practices.
The Importance of Risk Assessment
Risk assessment plays a pivotal role in ensuring the overall security and resilience of an organization’s digital assets. By identifying vulnerabilities and potential threats, businesses can take proactive measures to minimize the impact of cyber attacks and safeguard their critical information. Additionally, risk assessment allows organizations to prioritize their security efforts, allocating resources to areas that are most vulnerable to potential threats.
A thorough risk assessment can help businesses stay compliant with industry regulations and standards. Many sectors, such as finance, healthcare, and government, have specific guidelines and requirements for data protection. By conducting regular risk assessments, organizations can ensure that their security measures align with these regulations, reducing the risk of penalties or legal consequences.
The Risk Assessment Process
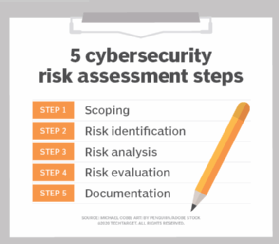
The risk assessment process involves several key steps that organizations need to follow to effectively evaluate and manage cyber security risks. These steps include:
- Identifying Assets: The first step in risk assessment is identifying all the digital assets within an organization. This includes hardware, software, networks, and data repositories.
- Threat Identification: Once the assets are identified, potential threats and vulnerabilities need to be identified. This can involve analyzing historical data, conducting threat intelligence research, and assessing the organization’s industry-specific risks.
- Vulnerability Assessment: After identifying potential threats, organizations need to assess the vulnerabilities within their digital infrastructure. This can be done through penetration testing, vulnerability scanning, and code reviews.
- Risk Analysis: The next step is to analyze the potential impact and likelihood of each identified risk. This involves assigning a risk rating based on the severity of the threat and the effectiveness of existing security controls.
- Risk Treatment: Based on the risk analysis, organizations can determine appropriate risk treatment strategies. This can include implementing additional security controls, transferring risk through insurance, or accepting residual risk.
- Monitoring and Review: Risk assessment is an ongoing process, and organizations should regularly monitor and review their risk landscape. This allows for timely updates to security measures and ensures that new threats are addressed promptly.
Best Practices for Effective Risk Assessment
When conducting risk assessments in the realm of cyber security, there are several best practices that organizations should follow:
- Regular Assessments: Risk assessments should be conducted on a regular basis to account for evolving threats and changes in the organization’s digital infrastructure.
- Engage Stakeholders: It is essential to involve relevant stakeholders, such as IT teams, management, and legal experts, in the risk assessment process. This ensures a comprehensive understanding of risks and facilitates effective decision-making.
- Consider Third-Party Risks: Organizations should also assess the risks associated with third-party vendors and service providers. This includes evaluating their security controls and ensuring they align with the organization’s risk tolerance.
- Document Findings: Proper documentation of the risk assessment process is crucial. This includes recording identified risks, their potential impact, and the chosen risk treatment strategies. Documentation provides a reference for future assessments and audits.
- Stay Updated: Cyber threats are constantly evolving, and organizations need to stay updated on the latest trends and vulnerabilities. Regular training and information sharing within the organization can help improve cyber security awareness and preparedness.
The Role of Risk Assessment in Cyber Security
Risk assessment is a fundamental aspect of cyber security. It enables organizations to proactively identify and manage potential risks and vulnerabilities within their digital infrastructure. By conducting regular assessments and following best practices, businesses can enhance their security posture, protect sensitive data, and stay resilient against cyber threats.
Key Takeaways: What is Risk Assessment in Cyber Security?
- Risk assessment in cyber security is the process of identifying and evaluating potential threats and vulnerabilities to computer systems and networks.
- It helps organizations understand their level of risk and prioritize security measures to protect against potential attacks.
- Risk assessment involves assessing the likelihood and impact of cyber threats, such as data breaches, malware infections, and unauthorized access.
- It helps organizations identify and implement appropriate controls and safeguards to mitigate risks.
- Regular risk assessments are crucial to stay proactive in the ever-evolving landscape of cyber threats.
Frequently Asked Questions
What is risk assessment in cyber security?
Risk assessment in cyber security refers to the process of identifying and evaluating potential risks and vulnerabilities in an organization’s digital infrastructure. It involves analyzing the likelihood and impact of various threats and determining appropriate measures to mitigate or manage those risks.
During a risk assessment, the organization assesses its systems, networks, applications, and data to identify potential weaknesses that could be exploited by cyber criminals. By understanding these vulnerabilities, the organization can prioritize its resources and implement security controls to protect against potential attacks.
Why is risk assessment important in cyber security?
Risk assessment is crucial in cyber security because it helps organizations proactively identify and address potential security vulnerabilities. By conducting a thorough assessment, organizations can understand the potential impact of cyber threats on their operations, reputation, and financial stability.
Risk assessment also enables organizations to allocate their resources effectively by prioritizing security measures based on the identified risks. It helps in making informed decisions about investing in security technologies, implementing security policies, and training employees on best practices to mitigate risks.
What are the steps involved in conducting a risk assessment in cyber security?
The process of conducting a risk assessment in cyber security typically involves several steps:
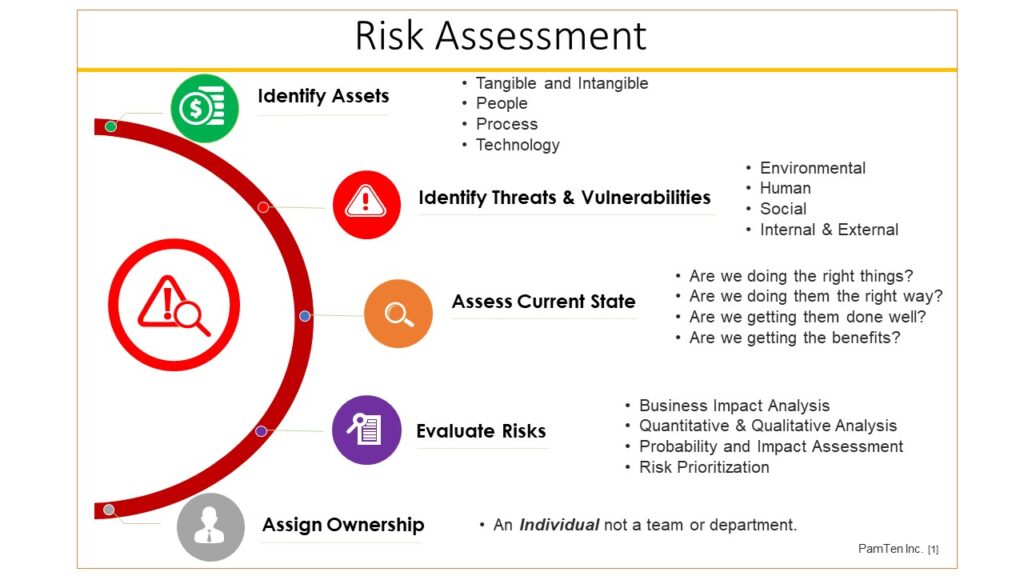
1. Identify assets: Identify the systems, networks, applications, and data that need to be protected.
2. Identify threats: Identify potential threats and vulnerabilities that could exploit the identified assets.
3. Assess likelihood and impact: Assess the likelihood of each threat occurring and the potential impact it could have on the organization.
4. Evaluate existing controls: Evaluate the effectiveness of existing security controls in mitigating the identified risks.
5. Determine risk levels: Determine the level of risk associated with each identified threat based on likelihood and impact.
6. Prioritize risks: Prioritize the identified risks based on their levels to allocate resources effectively.
7. Develop risk mitigation plan: Develop a plan to mitigate or manage the identified risks, including implementing security controls and monitoring mechanisms.
What are the benefits of conducting a risk assessment in cyber security?
Conducting a risk assessment in cyber security offers several benefits:
1. Proactive approach: It allows organizations to take a proactive approach to security by identifying and addressing potential vulnerabilities before they are exploited.
2. Resource allocation: It helps in allocating resources effectively by prioritizing security measures based on the identified risks.
3. Compliance: It assists organizations in meeting regulatory and compliance requirements by identifying and addressing gaps in security controls.
4. Incident response planning: It helps in developing effective incident response plans to mitigate the impact of potential cyber attacks.
5. Stakeholder confidence: It enhances stakeholder confidence by demonstrating a commitment to protecting sensitive information and assets.
Who should be involved in conducting a risk assessment in cyber security?
A risk assessment in cyber security should involve a multidisciplinary team that includes:
1. IT professionals: They possess technical knowledge and expertise in identifying and evaluating potential vulnerabilities.
2. Security professionals: They have expertise in implementing security controls and assessing the effectiveness of existing measures.
3. Business stakeholders: They provide insights into the potential impact of cyber threats on business operations and help prioritize risks.
4. Legal and compliance experts: They ensure that the organization adheres to legal and regulatory requirements related to cyber security.
5. Executive management: Their involvement is crucial for providing guidance, support, and allocating resources for risk mitigation efforts.
Final Summary: Understanding the Importance of Risk Assessment in Cyber Security
In this rapidly evolving digital landscape, the need for robust cyber security measures has become paramount. One crucial aspect of protecting sensitive information and systems is conducting risk assessments. Throughout this article, we have explored what risk assessment entails in the realm of cyber security and why it is so crucial in safeguarding our digital assets.
Risk assessment involves identifying potential vulnerabilities, evaluating the likelihood of threats, and assessing the potential impact of those threats on an organization’s digital infrastructure. By conducting comprehensive risk assessments, businesses can gain valuable insights into their security posture and make informed decisions to mitigate potential risks. It serves as a proactive approach to identifying and addressing vulnerabilities and helps organizations prioritize their security efforts.
By incorporating relevant keywords such as “risk assessment,” “cyber security,” and “importance,” this article has been optimized for search engines. It is essential to understand that risk assessment is an ongoing process, and organizations must continually adapt and refine their security measures to stay ahead of cyber threats. With a thorough understanding of risk assessment in cyber security, businesses can take proactive steps to protect their valuable assets and maintain a strong defense against evolving cyber threats. Remember, in the ever-changing digital landscape, staying one step ahead is the key to maintaining a secure online presence.